It's possible clone WhatsApp? Is it true that someone can take over our account, fool all the protection systems of the app and snoop into our conversations? Many people ask me, and so today I decided to deal with the subject to clarify, or rather, to try to understand, together with you, what are the behaviors and situations to which we need to be more careful.
Stealing the identity of a person on WhatsApp is unfortunately possible, it must be admitted, but it is an operation that always requires the "collaboration" of the victim. This of course does not mean that there are people willing to be spied on. It means, much more simply, that with adequate protection of your smartphone, putting a pinch of attention in what you do and applying the most common common sense rules you can prevent the vast majority of activities related to identity theft on WhatsApp .
To better understand what I am saying, let's try to analyze together some of the techniques used by cybercriminals to steal the identity of users on WhatsApp and see what are the countermeasures to be implemented to prevent them from being put into practice on our mobile phones.
Identity theft via WhatsApp Web / Desktop
As I also explained to you in my tutorial on how to use WhatsApp on PC, there are two very useful tools that allow you to use WhatsApp directly from your computer: one is Web WhatsApp which allows you to use WhatsApp on your computer using the browser, another is the official client of WhatsApp for Windows and macOS.
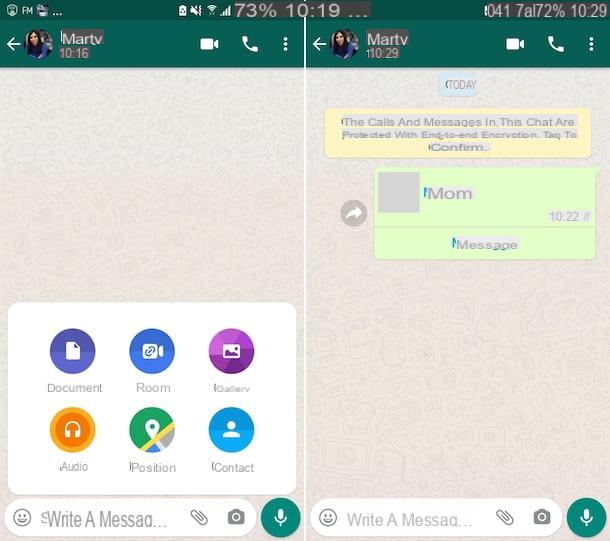
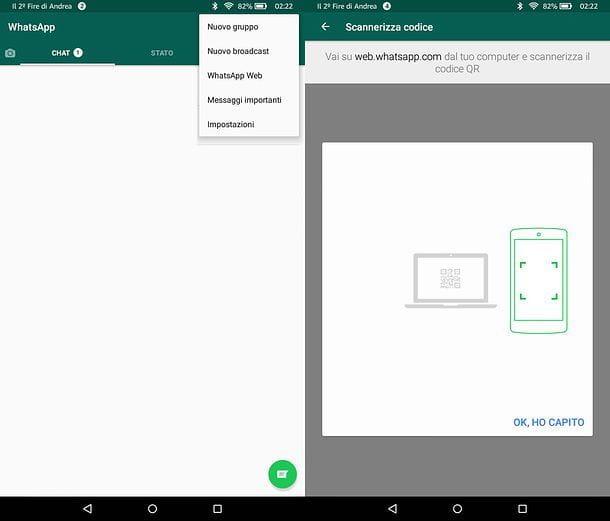
Both work in a very simple way. To use them, just frame a QR code with the smartphone camera and wait a few seconds for all the messages on the phone to be shown on the computer. And it is precisely this incredible immediacy that represents a potential risk for our privacy!
WhatsApp Web and the WhatsApp client for PC only work if the phone on which WhatsApp is installed is turned on and connected to the Internet, but they do not require the presence of the two devices under the same wireless network (so they work even if the smartphone is in a different location than the computer and is connected to the Internet via data network). Also, if you put the check mark next to the item Stay connected before logging in, it allows you to access your conversations without having to scan the QR code again.
In a nutshell, this means that an attacker could temporarily take possession of your mobile phone (a very trivial excuse, such as the need to make a call is enough), log in to WhatsApp Web or WhatsApp for PC on your computer (or even on a tablet with desktop mode enabled) and get continuous access to your chats.
How to protect yourself
To avoid the risk that someone can access your chats without permission via WhatsApp for PC, occasionally check WhatsApp Web / WhatsApp sessions for PC open on your account. Don't you know how to do it? Quiet, it's very simple.
To check which WhatsApp Web / WhatsApp PC sessions are open on your account, start WhatsApp on your phone and go to the menu Settings> WhatsApp Web / Desktop application. On Android, the settings menu appears by pressing the button (...) which is located at the top right.
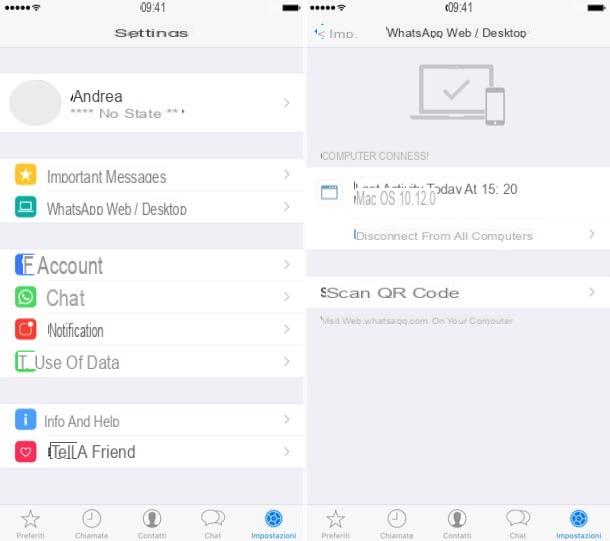
If you notice any suspicious activity, press the button Log out of all computers and all computers connected to WhatsApp Web will lose access.
Also, if you protect your device with a biometric recognition system, such as unlocking by face or one that requires a fingerprint, this method will also be required for confirmation purposes, for the connection. Web WhatsApp: in this way, therefore, no one will be able to access the service without your authorization.
Cloning of the MAC address
One of the finest techniques for clone WhatsApp is the one that involves cloning the MAC address of the victim's smartphone.
Il MAC address is a 12-digit code that allows you to uniquely identify all devices capable of connecting to the Internet: smartphones, tablets, PC network cards and so on. WhatsApp also uses it, together with the phone number, to identify its users and disguise it can fool the app's protection systems.

The good news is that cloning a MAC address isn't easy. It is necessary to be fairly familiar with IT means and, above all, to have free access to the victim's smartphone for a rather long period. Here, in short, all the steps that should be taken.
- Unlock your smartphone by rooting on Android or jailbreaking on iPhone;
- Install MAC address camouflage applications, such as CharmeleMAC and MAC Address Ghost on Android and SpoofMAC or MobileTerminal on iPhone;
- Get hold of the victim's smartphone and find out his MAC address (freely accessible from the menu Settings> Info of all major mobile operating systems);
- Camouflage the MAC address of your smartphone making it appear the same as that of the victim's phone;
- Install WhatsApp and activate it with the phone number of the person to be spied on (then using the victim's smartphone to receive the activation code of the app).
After this long process, the attacker could gain free access to the victim's WhatsApp account by bypassing the application's protection systems (which normally prohibit the use of WhatsApp on more than one phone at a time).
How to defend yourself
As already mentioned, clone WhatsApp disguising the MAC address is a very long and complex operation. However, it is better not to take unnecessary risks and take all those common sense measures that allow you to reasonably protect your account.
- Do not lend your smartphone to strangers and don't leave your phone unattended in public places. They are trivial, hackneyed, but always very valid advice!
- Protect your smartphone with a secure PIN. In this way, even if an attacker gets hold of our smartphone, he can hardly do anything about it. Here's how to set the PIN on Android, iPhone and Windows Phone.
- Android - go to the menu Settings> Security> Screen Lock. From here you can select the option PIN which allows you to set a numeric unlock code or the option Sequence which allows you to use a gesture (ie a "drawing" to be done on the phone screen) instead of the numeric code.
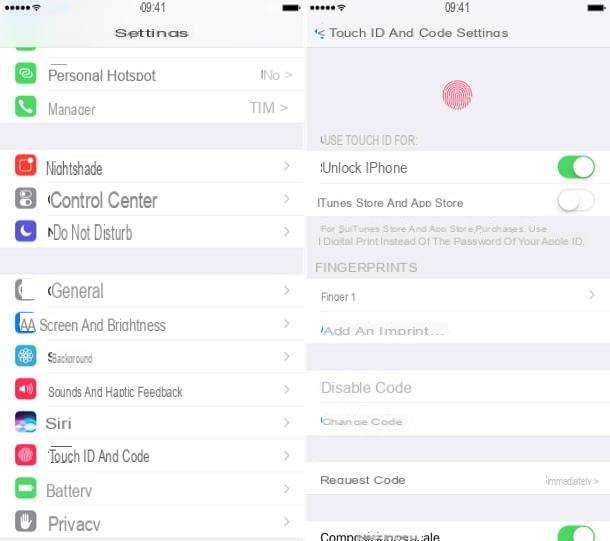
- iPhone - go to the menu Settings> Touch ID and Passcode I will select the voice Change codice.
- Windows Phone - go to the menu Settings> Lock Screen and activate the option Password.
- Prevent the display of SMS on the lock screen, so that any attacker cannot see the SMS with the WhatsApp verification code. Here's how it's done on Android, iPhone and Windows Phone.
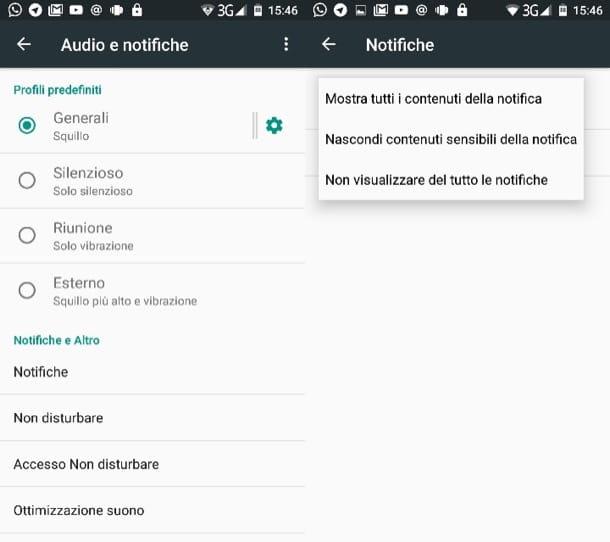
- Android - go to the menu Settings> Sound & Notifications> Notifications and set the drop-down menu With locked device su Hide sensitive notification contents (o Don't see notifications at all if you want to hide all notifications from the Android lock screen).
- iPhone - go to the menu Settings> Notifications> Messages and deselect the option Show in Lock Screen.
- Windows Phone - go to the menu Settings> Lock Screen and set to Nobody the drop-down menu Choose an app whose status you show in detail.
Security measures to avoid WhatsApp cloning
To conclude, let me give you some other advice on how to avoid WhatsApp cloning and / or intrusion into your chats. These are other measures of simple common sense, nothing complicated.

- I will avoid the public Wi-Fi withdrawal, which are often monitored by malicious people and could allow access to some sensitive data, such as WhatsApp conversations (in this regard, I invite you to use a VPN like NordVPN (which I told you about in depth here) or Surfshark to make the data of your connection always inaccessible by malicious people, providers or anyone). To learn more about this aspect, take a look at my post on how to spy on WhatsApp from a PC in which I explained to you in detail how the application's protection mechanisms work and what its weaknesses are.
- Check for spy apps on the phone. Operation that is not always easy to carry out, as many spy applications hide themselves so as not to be discovered by the user, but it costs nothing to try!
- Android - if you have an Android device, go to the menu Settings> Security> Device administrators and scroll through the list of all apps that are allowed to control the system. If any of these are suspicious, disable them and uninstall them.
- iPhone - if you have an iPhone unlocked by jailbreak, you can unmask the spy applications by opening the browser and connecting to the addresses localhost: 8888 e localhost: 4444 or by composing the code * 12345 in the dialer. If by performing one of these operations you see the management panel of an app appear to spy on the phone, open it immediately Cydia and delete all suspicious packages.