Is your corporate computer network secure? Check for any flaws with a thorough Penetration Test

The corporate IT structures are generally characterized by particular systems that protect the servers and PCs from any cyber attacks external or internal. However, in many companies there may be inadequate protections and unpleasant inconveniences, such as the theft of important information and data.
To prevent security problems and always guarantee maximum system reliability, we use the Penetration Test, a sophisticated procedure that allows you to check if the computer network is reliable. A series of in-depth tests are performed to determine if there are flaws, bugs, security gaps, identifying vulnerabilities and determining how to increase the level of protection.
can perform a thorough Penetration Test, to check the status of the corporate network. Through the use of the latest technologies in the industry, they can be found problemi hardware e bug software to ensure a higher level of security.
To perform a Penetration Test they are required specific equipment and advanced knowledge in the IT sector. In fact, even if it is a simulation of intrusion into the corporate network, it is necessary to have a good IT basis to perform the test.
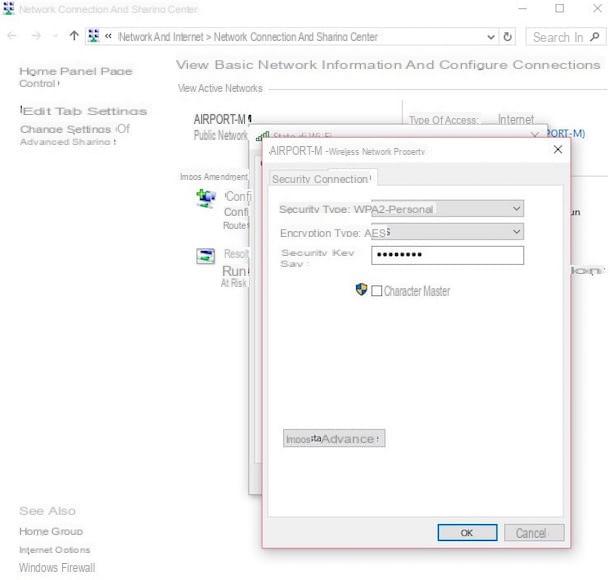
Technicians can carry out a first Penetration Test from the outside. In this situation, the weaknesses of the external network are verified, and an attempt is made to enter the system without having direct access to the servers. It is therefore a question of identifying vulnerabilities on the company's website, or bypass security of the wireless network through sophisticated techniques.
Another type of test is performed internally, therefore having direct access to PCs, notebooks, company servers. This type of attack allows you to simulate the malicious action of an employee who has access to the corporate network and could cause damage to the system. Also in this case a series of technical operations are performed to intrude on the network and access the central server. It therefore tries to bypass firewalls and other security systems.

Some very common flaws are missed software updates. The programs installed on the PCs, even the operating systems, must be constantly updated to the latest versions. In fact, the most recent versions fix security bugs and problems that could be a priority access route for bad guys who want to steal valuable data and information.
Once Penetration Tests have been carried out on the company's IT structure, both internal and external, a detailed report is generated with all the results obtained. The report is of fundamental importance, because it contains all the flaws and the critical points of the company network. It also indicates what are the priorities to be solved and what to invest in, to increase the level of security and ensure greater protection of sensitive data.
The Penetration Test activity is really very important if you want to know perfectly what are the vulnerabilities of your own corporate computer network and how to fix bugs and pain points.
Protecting the company from cyber attacks: conclusions
If you need to verify the security of the IT systems internal and external to your company, you can contact us for advice. We can perform a Penetration Test of the corporate network, evaluating what are the optimizations to be performed and how to improve the protection.