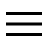Index
Techniques used to sneak into another PC
As I mentioned earlier, the first part of my guide will focus on the techniques used by cybercriminals for enter another PC secretly. You will soon discover that, in most cases, the primary access channel is… a moment of distraction on the part of the rightful owner of the computer! Do not you believe it? I'll show you in a few minutes.
Backdoor

Without a shadow of a doubt, one of the most widespread and exploited techniques for obtaining unauthorized access to third-party computers involves the use of backdoor (this word, translated into cittàn, means service door). The definition is not accidental at all: this type of attack, in fact, consists in creating a sort of communication channel direct between the victim's computer and the cybercriminal's device, without the former noticing anything.
By doing so, cybercriminals have the ability to remotely control the computer, without being physically present in front of the machine, making it perform the most varied operations (create and delete files, carry out other cyber attacks, create real botnets and so on) without getting caught.
Typically, backdoors are spread and activated through particular malicious software, called trojan. These programs are usually made to install on the victim's computer by the latter, with deception: for example, they are inserted into apparently harmless software but which actually hide malicious code inside them (for this they are called trojan horse, i.e. Trojan horses) and operate in the background, or are spread via email with an invitation to click on infected links.
Once installed, the trojan bypasses system protections exploiting the ports generally used by users for the operation of P2P programs (such as BitTorrent clients) or to provide remote assistance. Fortunately, the protections active by default in the most modern computer operating systems (Windows 10 and macOS Mojave, for example), are able to neutralize most of the backdoors but, in cases like these, it is not possible to guarantee the absolute invulnerability.
Keylogger

Another widely used technique to illegally access computer systems is to use defined programs keylogger: these, generally well hidden and therefore invisible, record everything that the unsuspecting user types on the keyboard, and then send the information via e-mail directly to the cybercriminal on duty.
These programs, in addition to allowing unauthorized access to computers, are extremely dangerous for the integrity of your personal data. The information received from the criminals, in fact, could contain Password of Internet sites (social networks, home banking portals and so on), credit card numbers, secret codes, excerpts from conversations and much more: in short, whatever is typed via the keyboard!
If you remember well, I had already told you about keyloggers in my last tutorial, in which I showed you, for information purposes only and with the specific intention of teaching you to defend your data, how to spy on a computer in this way.
Far less common (but equally effective) than software keyloggers are the so-called keylogger hardware, that is, small devices that stand between the keyboard and the computer and record everything that is typed; sometimes, these little gizmos also have features for automatically sending recorded data. Unfortunately, it's not easy to spot a relatively small and strategically placed hardware keylogger.
Social engineering

It may be hard to believe, but it is possible to gain unauthorized access to a computer even "in the open". This technique, called social engineering (o SOCIAL ENGINEERING, in cittàn), tends to exploit the inexperience, naivety or, sometimes, the haste of the victims. How? I'll explain it to you right away. Typically, the cybercriminal, often aided by an accomplice, physically approaches his potential victim and, with an excuse, asks him to use the computer.
If the user in question agrees to this, the cybercriminal takes advantage of the situation - often with the help of an accomplice who distracts the one who, at this point, has become the victim - to install a "legitimate" remote control program, like the ones I told you about in my guide on how to remotely connect to another PC, or to install one backdoor or keylogger. Once the job is done, the criminal will have plenty of time to remotely monitor the victim's activity undisturbed.
How to protect your PC from intruders
Now that you are aware of the most used techniques to sneak into another PC, it's time to tackle the most interesting part of this guide, the one dedicated to defense techniques from external attacks: below you will find everything explained in detail.
Use common sense

Before even talking to you about software solutions, I believe it is my duty to give you some advice which, in my opinion, is fundamental: the most important technique to prevent your computer from falling victim to cybercriminals is, of course, that of use common sense.
Therefore, in order to avoid unintentionally installing a trojan or keylogger, I strongly advise you to don't open files you don't know where they come from: therefore, do not start programs downloaded from untrustworthy sites, do not open unexpected e-mail attachments (especially if accompanied by visibly dubious messages) but, above all, avoid connecting USB sticks or other untrusted storage devices to the PC.
Also, don't let strangers have easy access to your computer: if someone asks you for help, take care to provide it by operating yourself from your PC. A moment of distraction could be fatal to you!
Use a firewall

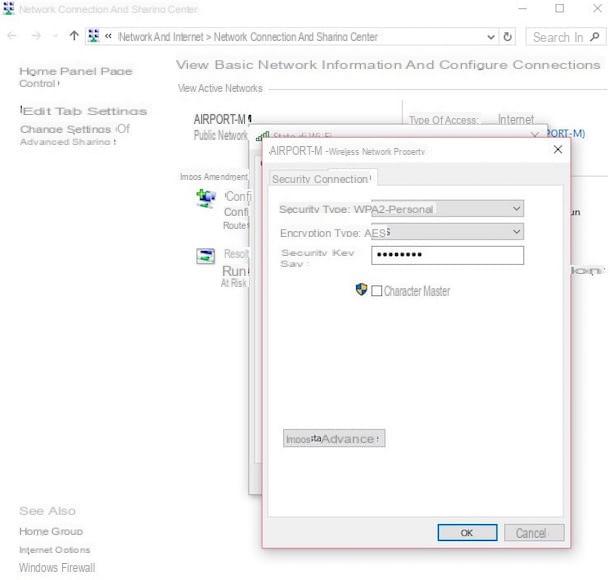
A great way to inhibit threats like trojan e backdoor is to rely on a good one firewall: if you don't know what I'm talking about, know that a firewall is nothing more than a security system (be it a program or a device) that prevents unauthorized software and hardware from communicating with the outside.
Most modern computer operating systems include a firewall, usually turned on by default: PCs Windows, for example, they rely on Windows Defender, a program that offers a good level of protection. To check that the latter is active on your computer, open the Control Panel calling it up from the menu Homeclick sulla voce System and security and, subsequently, su Windows Defender Firewall/Windows Firewall.
At this point, check the color of the icon shield corresponding to the items reti private e guest or public networks: if this is it green, then the firewall is active. If, on the other hand, the shield is colored red, it means that the firewall is not currently active - to remedy the problem, click on the link Enable / Disable Windows Defender, then select both options Activate Windows Defender and click on the button OK to confirm the changes. If you are not satisfied with the integrated solution in Windows, you can give a chance to third-party alternatives such as Windows Firewall Notifier and Comodo Personal Firewall.
Also Mac integrate an excellent firewall system: to check that this is active, log in to System preference (the icon in the shape ofgear located in the Dock bar), go to the section Security and Privacy> Firewall and, if this is not active, enable it by clicking on the button Turn on Firewall. Alternatively, you can turn to third-party firewall solutions, such as Radio Silence or Little Snitch.
Rely on good antivirus
Besides the firewall, another great way to protect yourself from cyber threats is to install a good one antivirus on your computer: with real-time monitoring capabilities, it's a great way to keep your computer safe from trojan and in some cases, keylogger, getting rid of it practically instantly.
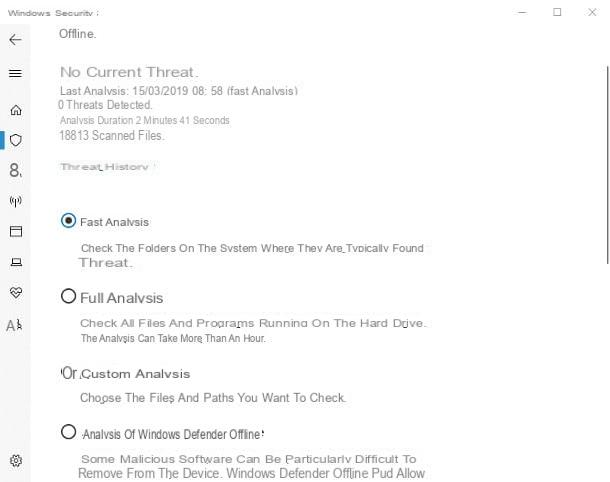
You must know that, contrary to what is generally believed, one of the best antiviruses around is Windows Defender, the solution included “as standard” in the most recent versions of Windows. Defender is usually active by default and continuously monitors the system, automatically performing scans from time to time; if, however, you want to make sure that it is actually enabled (and, if not, proceed with activation), carefully follow the instructions I gave you in my tutorial on how to activate Windows Defender.
To perform a manual system scan, open the Start menu and search Virus and threat protection (o Windows Defender, on operating systems prior to Windows 10) using the appropriate search field, wait for the antivirus to be loaded, indicate whether to perform a scan Veloce, Complete, Personalized or Offline via the menu Analysis options and, to start scanning, click on the button Quick analysis / Full analysis /Start analysis. Where active threats are actually identified, you will receive a report and will be invited to proceed with their permanent removal.
If you find Defender a bit reductive for your expectations, you can also turn to third-party antivirus, such as Avast o Bitdefender, both available in both free and paid Premium versions: to learn more about the subject, I urge you to read my article on the best antivirus.
As regards the MacNormally, the protections active on the operating system are more than enough to protect the computer from cyber threats (widespread in much less number than what happens on Windows), so I would suggest you take advantage of on-demand scanning tools. If you want some more knowledge on this topic, or would like an overview of the tools you can use in this sense, I suggest you read my guide dedicated to the best antivirus for Mac.
Perform periodic anti-malware scans
Another good practice to protect your computer from unwanted access is to perform scans using software at regular intervals. anti-malware. By doing so, you should be able to track down those cyber threats that the antivirus failed to detect and / or neutralize, thus preventing cybercriminals from taking control of your computer remotely.
In my opinion, one of the best free anti-malware solutions currently available is Malwarebytes Antimalware: it is a software available on the Windows and macOS platform (but also as an app for Android), constantly updated, easy to use, and able to detect and destroy even the most recent threats. As I have already mentioned to you, it is a free basic software, which however also includes a paid version with additional features (e.g. the real-time control system).
In any case, you can download Malwarebytes Antimalware by connecting to this website and pressing the button Download now placed inside; completed the download, start the file obtained and act in the most appropriate way, based on the operating system you are using.
- These poisons are Windows, premium pulsating Yesselect l 'cittàn from the language selection menu and, to proceed, press the buttons OK, accept and install e end. At the end of the setup, press the yellow button Start now to take advantage of the 14-day trial period of the Premium version, or on the button Not now to start the free version of the software.
- Stai using MacOS, open the package.pkg previously downloaded, presses the button three times in a row Continue, then on the buttons Accept e Install and enter the administration password of the Mac. Once this is done, click on the button Install software and, finally, on the buttons Close e Move. At the end of the setup, you will be asked whether or not to start the trial period of the Premium version of the program: if you do not want to try it, press the button Not Now placed at the bottom.
Once the main interface of the program has been loaded, you just have to start a scan immediately by pressing the button Scansione/Scan Now located in the central part of the proposed screen: keep in mind that, depending on the amount of data on the computer and its performance, the scan could take from 20 to 60 minutes.
Once the analysis is complete, where threats were detected, a list will be shown with their description and location on the disk: to neutralize them and move them to a safe place on the computer, called quarantine, check that they are marked with a check mark and press the button Apply actions.
If, on the other hand, you want some files to be ignored (because, for example, you are aware that they have generated false positives), select the item Ignore from the drop-down menu located next to them, continue by clicking on the button Apply actions And that's it. For additional information on how Malwarebytes Antimalware works, I invite you to consult the specific tutorial I have dedicated to this software.
If Malwarebytes Antimalware failed to meet your expectations, you can take a look at my guide dedicated to the best anti-malware, in which I showed you valid alternatives to the software just examined.
Avoid unknown Wi-Fi networks

I am perfectly aware that, at times, a freely usable wireless network could be a lifeline, however you have to consider this possibility in another perspective: unknown Wi-Fi networksin fact, they can grant cybercriminals access to your personal data.
Exactly as I explained to you in my post on how to sniff a wireless network, non-password protected networks can be “monitored” by hackers, in order to steal information in transit; if properly combined, the information obtained could represent a good springboard for unauthorized access to connected computers.
This risk, however, also exists for protected Wi-Fi: a hacker could purposely build an unsecured wireless network, with a simply guessable password, to analyze the data in transit on it and use it in his favor.
So, if you really need to connect to the Internet via your laptop, when you are not at home, you'd better use your mobile phone as a modem, creating a hotspot: in this way, you would have the possibility to connect the laptop to the network using the Internet connection of the SIM present in the smartphone. Of course, make sure you have an adequate data plan for the purpose, in order to avoid finding yourself without Giga at the most beautiful!
How to sneak into another PC