Spy apps

Let's start with the burning topic related to spy-applications. As also highlighted in previous articles, for example those on applications for spying on mobile phones and on techniques for spying on Android smartphones, there are apps that allow you to monitor and even control smartphones remotely.
This means that yes, potentially someone could spy on your activities remotely, "capture" everything you see on the screen, everything you type on the phone keypad and even control the device remotely. But fortunately, in the vast majority of cases, physical access to the smartphone is required to do all this.
In other words, if you prevent bad guys from getting their hands on your phone (or at least having free access to the device's operating system), you can minimize the risk of being spied on with one of these apps. Clear? So here are some tips on how to prevent this problem.
- Don't lend your smartphone to people you don't trust and do not leave the device unattended for a long time. I know, they are tips of a disconcerting banality, but often it is the lack of attention to detail that plays tricks!
- Prevent anyone from having free access to your smartphone by setting a secure PIN for the lock screen. Up Android just go to the menu Settings> Security> Screen Lock I will select the voice PIN from the screen that opens. Up iPhone you have to go to the menu Settings> Touch ID and Passcode (o Face ID and Code) and will select the voice Change codice. If your device supports fingerprint and / or facial recognition unlocking, use it as it is an even more secure method.
Another piece of advice I would like to give you is to go to the app management panel (Settings> Apps> All su Android e Settings> General> iPhone Free Space su iPhone) and check if there is any "suspicious" name, that is some app with an unknown name that may be hiding a spy app.
Unfortunately it must be said that many of the smartphone monitoring applications are able to hide from the system menus, so you may not be aware of their presence. In such situations, if you suspect that someone is monitoring your activities but you do not see “suspicious” applications in the mobile phone menus, you just have to format the device and delete all the data in its memory. Find out how to do it in my tutorials on how to reset Android and how to reset iPhone.
Furto d'identità

Il identity theft is one of the most used techniques for check another's WhatsApp. It consists of tricking the app's security systems by pretending to be another person, and thus accessing their conversations. There are several ways to land this kind of "hit". Among the most common methods is the use of WhatsApp Web / Desktop, the computer version of WhatsApp that allows you to exchange messages from the browser or the official client of the service, and the MAC address cloning. Let's take a closer look at both of them.
WhatsApp Web / Desktop
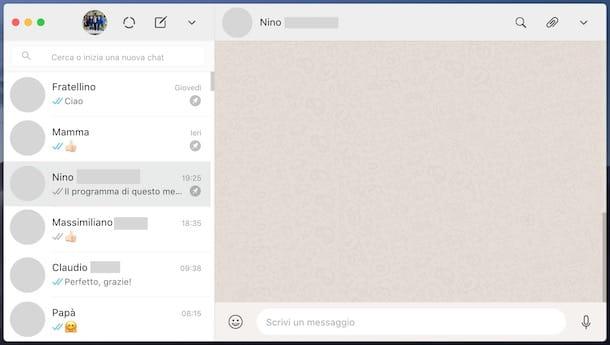
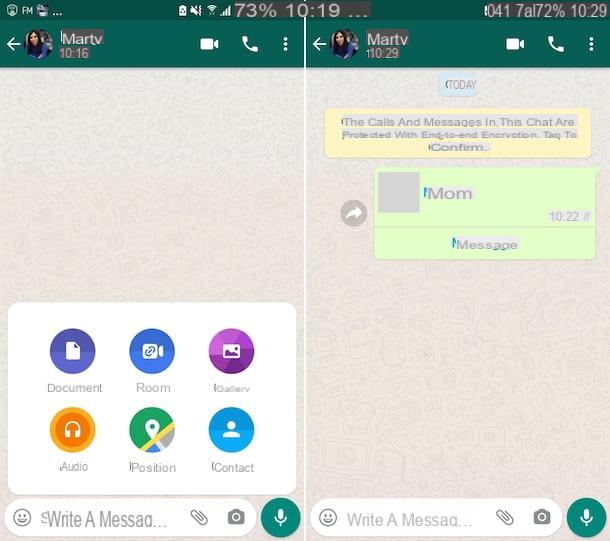
As I also explained to you in my tutorial on how to use WhatsApp on a PC, WhatsApp Web works using the smartphone as a "bridge". It is a simple interface for the application installed on the phone, which does not work if the device is not on and connected to the Internet, but… there is a but.
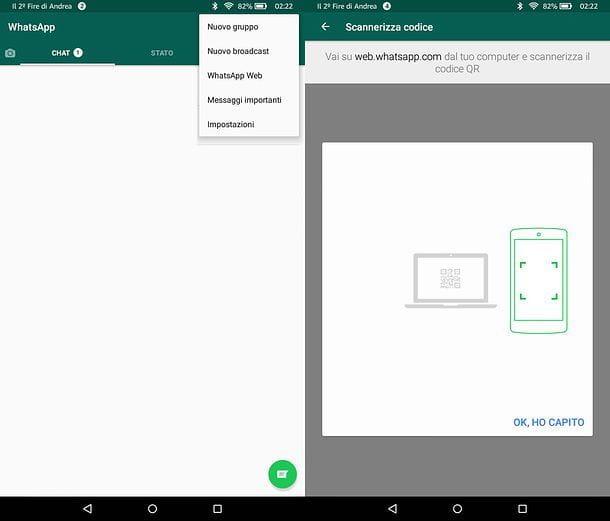
WhatsApp Web works even when the phone is not connected to the same wireless network as the PC, so even if it is away from the computer and connected to the Internet via the 3G or 4G LTE data network. Another potentially "critical" aspect concerns the fact that to access the service it is enough to scan the QR code displayed in the browser once with the mobile phone camera: by checking the option Stay connected, subsequent accesses take place completely automatically.
These two factors could allow an attacker to steal your smartphone, log in to WhatsApp Web, and gain access to your account from your computer (or tablet, using WhatsApp Web's desktop view mode). All in seconds!
To prevent this type of threat, put into practice the tips I gave you earlier (i.e. don't lend your phone to strangers and use a secure unlock PIN) and from time to time take a look at active WhatsApp Web sessions on your account. Also, remember to activate an unlocking system on your device via a biometric authentication method (for example Face ID/touch ID on iOS): in this way you will prevent any unauthorized access as it will also be required, for confirmation purposes, to connect to WhatsApp Web / Desktop.
To check the active WhatsApp Web sessions on your account, open the application and select the item Web WhatsApp from the menu (...) (or from the card Settings, if you are using iOS). If you detect any "suspicious" activity, press the button Log out of all computers and all PCs connected to your WhatsApp account will automatically lose access.
In addition, always keep an eye on the notifications that arrive on your smartphone: in the latest versions, in fact, WhatsApp automatically notifies the user when a new access is made to WhatsApp Web or WhatsApp Desktop.
Clone the MAC Address
Another technique by which cybercriminals can perpetrate identity theft is cloning the MAC address of the victim's phone. If you don't know, the MAC address is a 12-digit code that uniquely identifies all devices capable of connecting to the Internet and WhatsApp uses it, together with the telephone number, to identify its users.
If an attacker manages to discover the MAC address of your smartphone (information easily found in the menu Settings> Info) and disguise that of his phone so that it looks the same as it (there are applications such as MAC Address Ghost su Android e SpoofMAC su iPhone that allow you to do it quite easily), you can install a "cloned" copy of WhatsApp, activate it with your phone number and access your account without the application detecting the use of the same account on two different mobile phones (operation which, as you may already know, it is normally not allowed). For more information on this type of attack and the "counter moves" you can implement to counter it, read my tutorial on how to clone WhatsApp.
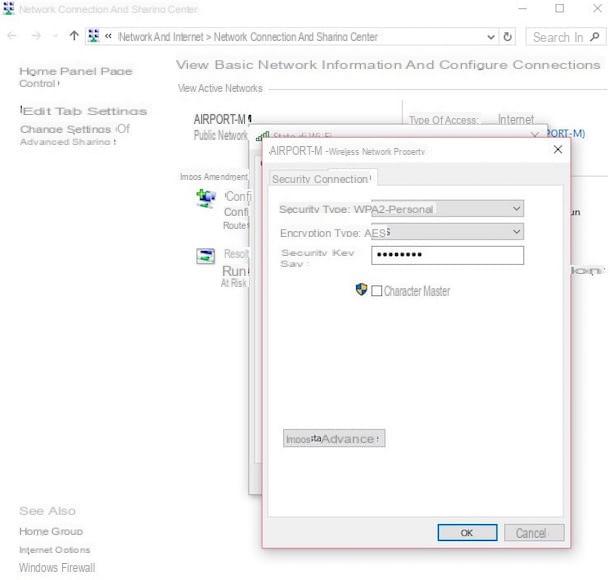
Wireless sniffing

As I explained to you in my post on how to sniff a wireless network, there are applications, even free, that allow you to "capture" all the data circulating on a wireless network in order to violate the privacy of others.
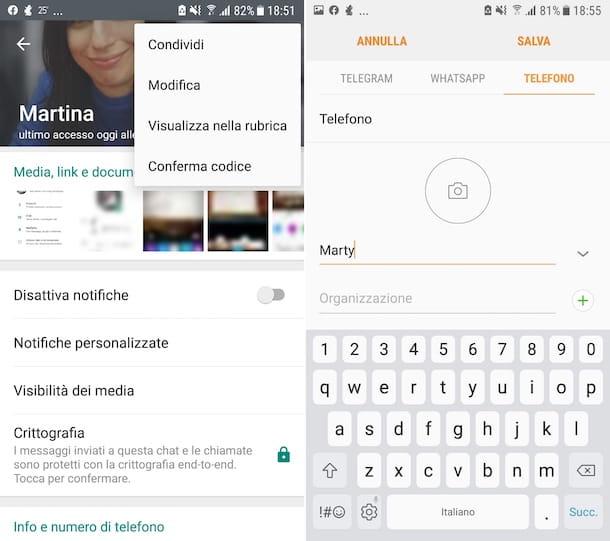
WhatsApp effectively counteracts this threat by adopting the end-to-end encryption for all communications. With end-to-end encryption, messages, calls and other content are encrypted using a pair of keys (one public, which is shared with the interlocutor and encrypts outgoing communications, and one private, which instead resides only on the smartphone. of each user and decrypts incoming communications) and travel in an encrypted manner also on the service's servers. This means that only the legitimate senders and recipients can read its contents, but it is fair to have some small doubts regarding its implementation.
A study published in April 2015 showed that only messages sent to and from Android were encrypted using end-to-end encryption. Other operating systems used a system based on the RC4 algorithm, which is notoriously vulnerable to sniffing attacks. Now the situation is different, as all platforms adopt end-to-end encryption, but there is another problem that must not be forgotten. WhatsApp is software closed source. This means that we cannot fully analyze its source code and we cannot know if the end-to-end encryption implementation was done correctly, if the system works on all platforms or if, perhaps, it has been disabled in some. nations under pressure from local governments.
In short, we must trust and cross our fingers so that there are no "holes" in the implementation of the encryption systems in question. The only thing we can actually do to defend ourselves against this type of risk is avoid using public Wi-Fi networks (which as known are the preferred hunting ground for "spies") or use other messaging applications, perhaps open source, with end-to-end encryption of proven reliability.