Kali Linux

Kali Linux is not a 'application to find WiFi passwords: it is an operating system, a Linux distribution to be precise, which includes all the tools necessary to test the security of wireless networks. It can be used in "live" mode by anyone USB pendrive o diskette or it can be installed in one virtual machine. It is compatible with most computers currently in circulation and requires no special hardware components, if not one network card equipped with support for the monitoring function.
The operation of Kali Linux, it must be said, is not among the most intuitive: it should be used mainly by command line, but on the Net there are many tutorials (also in cittàn) that explain in detail how it works. For obvious reasons, I will limit myself to giving you just a brief smattering of the main commands that allow you to test the security of wireless networks.
Once Kali Linux boots, you need to open the terminal and type the command airmon-ng to find out if your network card supports the monitoring function. The name of the network card is displayed under the entry Interface and usually it is wlan0. If your PC's network card does not have the monitoring function, you need to purchase an external network card. The external network card is also essential if you intend to use Kali Linux via virtual machine (eg via VirtualBox).

Once you have verified the adequacy of your network card for monitoring surrounding networks, issue the command airmon-ng start wlan0 to activate the monitoring function (instead of wlan0 you have to enter the name of the network card obtained with the previous command). You will get an output of the type monitor mode enabled on mon0. mon0 is the name of the monitor interface, keep this in mind because you will need it soon.
Now you need to issue the command airodump-ng mon0 (where instead of mon0 the name of the monitor interface obtained with the previous command must be entered) to start the control of the surrounding networks. As the seconds pass, you will see the list of available networks appear.

So find the name of the network to "pierce" and stop the monitoring of Kali Linux using the combination of keys Ctrl + C. At this point, give the command airodump-ng -c [Wi-Fi channel] --bssid [network name] -w / root / Desktop / [monitor interface] where instead of [Wi-Fi channel] you must enter the value CH of the net to be attacked, instead of [network name] you must enter the value BSSID of the net to be attacked and instead of [monitor interface] you must enter the name of the monitor interface (eg. mon0) and the network attack phase will begin.
The attack will be successful when the four-way handshake, which is the process by which the router of the network to be attacked receives the new devices. If the four-way handshake does not occur within a few minutes, open a new Terminal window and give the command aireplay-ng -0 100 -a [BSSID router] -c [BSSID client] [monitor interface] to force it to run.
When the attack is launched, you will find files on the desktop, which if properly treated using dictionary files available online, will allow you to trace the key of the attacked wireless network.
WIFI WPS WPA TESTER (Android)
Have you ever heard of the WPS (Wi-Fi Protected Setup)? This is the technology that allows the router to communicate with signal repeaters, printers and other wireless devices simply by pressing a button. Well, know that it is not free from security holes. Indeed, in the past it has been the subject of numerous attacks and still today there are apps that allow you to "pierce" the Wi-Fi networks by exploiting the vulnerabilities of some routers and access points linked to the WPS system.
Among the most effective applications that allow you to violate wireless networks via WPS I point out WIFI WPS WPA TESTER for Android which is completely free and is very simple to use. Its only "flaw", if we want to consider it that way, is that it does not work with all routers and access points. It also needs the root to be able to work at 100%: without the root it does not work on Android versions prior to 5.0 and does not allow you to view the WPA and WEP keys on later versions of the green robot operating system.

That said, to attack a network with WIFI WPS WPA TESTER, all you have to do is start the app, press the button Conceded to grant it root permissions and press the button Accept to accept the conditions of use. Then you have to "tap" on theicon with two arrows located at the top right to start scanning the surrounding networks and identify the network to attack. If no network name appears, it means that none of the surrounding networks use the WPS system and therefore are attackable.
Once you have found a potentially vulnerable network, select it and choose whether to attack it using the system automatic, an Personalized PIN or by choosing one of the PIN “manual” listed at the bottom of the screen. If you are told that the network is probably not compatible, very unlikely the attack will be successful (even if the router uses the WPS system).
iWeb PRO (iOS)

Unfortunately, there are no advanced applications such as WIFI WPS WPA TESTER for iOS. One of the few apps, or rather, of the few tweaks that come close to the functioning of the latter is iWep PRO which only works on devices subjected to the jailbreak procedure and only with versions of iOS up to 9. It supports WEP encryption systems and WPA but is not compatible with all routers and access points.
To use iWep PRO, all you have to do is download it from Cydia (the alternative app store available on jailbroken devices), start it and select one of the vulnerable networks (those highlighted in blue). Within a few seconds, if the network is indeed attackable, you should be able to see its passkey.
Fastweb.Alice.WiFi.Recovery (Android)

Some time ago, the default access keys of some Alice and Fastweb routers ran out on the Net. Fastweb.Alice.WiFi.Recovery is a free app for Android that, by drawing on that database leaked online, manages to "pierce" the wireless networks of those old routers that have not changed the access keys. Fortunately, it now works with very few routers, but believe me, there are still some old networks and old modems / routers on which the default passwords have not been changed!
Wifi-Pass (iOS)

Wifi-Pass is the iOS variant of Fastweb.Alice.WiFi.Recovery. It is therefore a free app that allows you to "pierce" the networks of the old Alice and Fastweb routers on which the default keys have not been changed. Its effectiveness is limited, but it is freely available on the App Store and does not require jailbreaking, so it may be worth a try.
WirelessKeyView (Windows)
Isn't your goal to test the security of a wireless network? Do you simply want to retrieve the key of a network that you used on your PC but you do not remember the access credentials? No problem, there is WirelessKeyView.

If you have never heard of it, WirelessKeyView is a free software for Windows which, once downloaded and run (requires no installation), shows the list of wireless networks stored on the PC with the relative access keys. It works on all versions of Windows and with any type of wireless network.
To download WirelessKeyView on your PC, connected to its official website, scroll the page almost to the bottom and click on the item Download WirelessKeyView for x64 (or on the item 32-bit WirelessKeyView download if you are still using a 32-bit version of Windows). Then open the zip package that contains the program, extract the contents into any folder and run the executable WirelessKeyView.exe. You will find all the networks stored on the PC and the relative access passwords directly in the main program window.
Keychain Access (Mac)
MacOS also stores the passwords of wireless networks (unless the user prevents it) and allows you to trace them. To take advantage of this possibility just use Portachiavi access, an application included “standard” on all Macs and found simply by opening the folder Other from the launchpad.

To find out the password of a Wi-Fi network with Keychain Access, start the latter, select the items System e Password from the left sidebar and double-click on the name of the network of your interest. In the window that opens, put the check mark next to the item Show the password, type the password of your user account on macOS and that's it!
WiFi Key Recovery (Android)

Do you have an Android smartphone or tablet and would you like to recover the password of a network used on it? No problem, if you are rooted, you can install WiFi Key Recovery: a free app that, similar to the ones I just reported to you for Windows and macOS, shows a complete list of the networks used on the device and the relative access keys . Explaining how it works is superfluous: just start it and grant it root permissions by pressing the button Conceded. The list of networks stored on Android and their access keys is shown on the main screen of the app.
Wi-Fi Passwords (iOS)

If you have an iPhone or an iPad, you can recover the passwords of the wireless networks stored on the latter by jailbreaking and installing the Wi-Fi Passwords tweak from Cydia. The operation of the tweak is similar to that of WirelessKeyView on Windows, WiFi Key Recovery on Android and the like: just start it and you will immediately find yourself in front of the list of networks stored on the device with the passwords to access the latter.
How to protect yourself from applications to find WiFi passwords
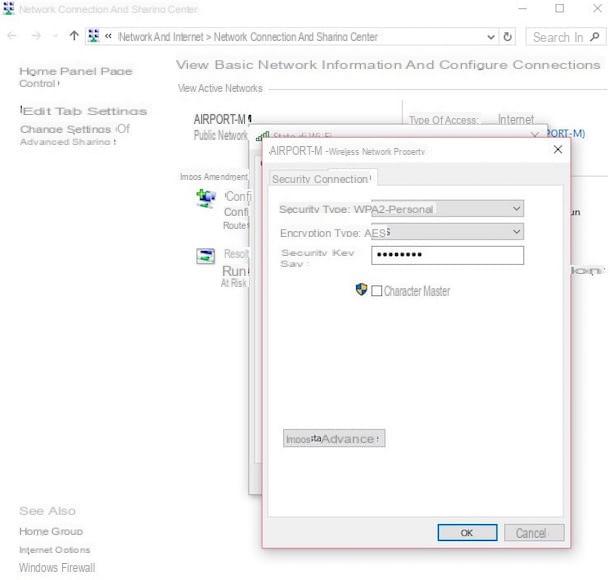
At this point in the tutorial, you are surely wondering how to sleep reasonably soundly and protect your wireless networks from potential attacks. Well, what you need to do is access the management panel of your router (by typing 192.168.1.1 o 192.168.0.1 in the browser), enter the access data to the browser (which should be admin / admin o admin / password) and apply the following changes.

- Go to the section relating to wireless network and configure your network to use the encryption system WPA2-AES and a hard-to-guess passkey of 12-16 characters, including lowercase letters, uppercase letters, numbers, and special characters. If you have very old devices and some of them can no longer connect after changing the encryption method of the wireless network, use the system WPA/WPA2 – TKIP/AES which is reasonably secure and allows access even to older devices. Stay away from the system absolutely WPA which is extremely dated and is easily attacked by a lot of apps. If your router also handles 5GHz networks, set up a secure encryption method and strong password for both 2.4GHz and 5GHz networks.
- If you don't use it, turn off the technology WPS which as we have seen above can be used to attack some vulnerable router models.
- If you haven't already done so, go to the security settings or in the General Settings router and change the default username and password combination to access the device settings. This will not increase the security of the wireless network but will prevent unauthorized access by any malicious people who could physically get their hands on the router.
As you may have noticed, in this last paragraph I have not been very precise in my indications. This is because each brand of modem / router has a configuration panel structured in a different way and therefore the items in the various menus may vary slightly. For more precise information, try to consult my specific tutorials dedicated to the various models of modems and routers.
- How to configure TIM / Alice routers
- How to configure Fastweb routers
- How to configure Infostrada routers
- Come configurare i router Netgear
- Come configurare i router D-Link
- Come configurare i router TP-Link