How to find hidden viruses in Windows PC
You rely on the operating system Windows? Perfect, then this is the most suitable section for you: below I will show you several ways to go for find hidden viruses in your PC relying on free and easy-to-use solutions.
Rely on a good antivirus
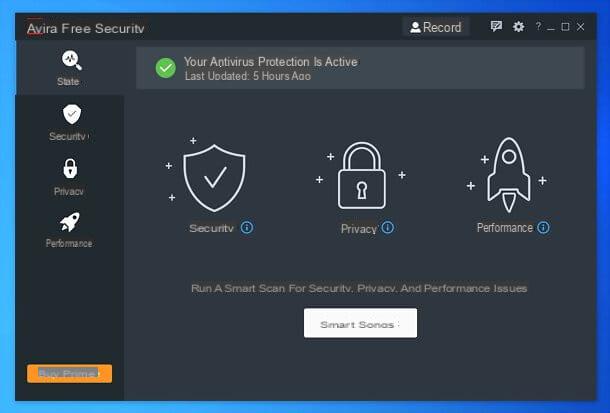
If, despite the presence of Windows Defender (the antivirus built into Windows), you continue to experience rather strange behavior on the part of the computer, you should consider installing third-party antivirus software that is efficient and, if possible, inexpensive.
In this regard, I suggest you take a look at Avira Free Security, a system security suite that includes a real-time protection against viruses, ransomware and other malware; a VPN to encrypt the connection, disguise your geographical position and browse securely even on Wi-Fi networks (with 500MB of free traffic per month); a secure browser, One password manager and a wide range of tools for optimize your PC (e.g. delete unnecessary files, clean the registry, delete files securely, fix system privacy issues, and much more).
Other points in favor of Avira Free Security are the effectiveness of its scanning engine (awarded several times by the well-known antivirus comparator AV Comparatives), theabsence of advertising banners and the guarantee by Avira that user data is neither sold nor shared with government agencies, Big Tech, advertising networks or other entities.
Avira Free Security, as mentioned, is a free product, but to access some advanced tools (e.g. those to manage processes and network traffic, defragment the registry, clean the disk and optimize energy saving in an advanced way, recover deleted files and encrypt / decrypt files) you need to subscribe to one of the paid plans between Internet Security (starting from € 6,95 / month or € 64,95 / year, usable on up to 5 devices), Premium (starting from 9,95 euros / month or 99,95 euros / year, usable on max) or Prime Family (starting from € 12,95 / month or € 129,95 / year, usable on up to 25 devices).
Avira Free Security is compatible with all popular versions of Windows and also with MacOS (although on Mac it doesn't have real-time protection and system optimization tools). To download it to your PC, connect to its official website and click on the button Download now. Then open the .exe file got it and click the buttons Yes e Accept and install.
Avira will position itself in the lower right corner of the screen and inform you about the status of the installation. Once the suite has finished downloading and installing automatically, agree to run one Smart scanning of the system and you will discover, in a few seconds, i privacy issues, performance, virus, app obsolete e network threats possibly present on the PC.
Once the scan is complete, click on the button Fix problems, to correct all problems detected by Avira at the same time, or on the button Show details, to choose the individual problems to be corrected. Please note that the free version of Avira, at this juncture, only allows you to delete unnecessary files and registry entries.
At this point, you just have to browse all the tabs on the left and use the various tools offered by the suite: the tab State, for example, allows you to have a general overview of the security, privacy and performance status of the system (and allows you to perform other Smart scans), while the Safety It allows you to start scans for viruses and malware, adjust protection options, manage the firewall and check for updates for the programs installed on your PC.
The board Privacy contains tools dedicated to web protection (through which to activate the Avira Safe Shopping browser extension, to protect yourself from fraudulent sites and online tracking), the VPN, the Avira password manager, the Shredder to delete files safely, Avira's customized Opera browser (with integrated Safe Shopping and Avira VPN extensions), Avira's password manager (to keep passwords securely) and the tool to adjust system privacy settings.
Finally, there is the tab Performances containing the system optimization utility Avira System Speedup to free up disk space, save battery, speed up your PC, update drivers, and more. Everything is extremely intuitive: just click on the respective buttons and follow the instructions on the screen, which are completely in cittàn.
If you need more information, feel free to consult my tutorial on how Avira Free Security works: there you will find all the information you need on the features and use of the suite.
Using a "rescue disk"
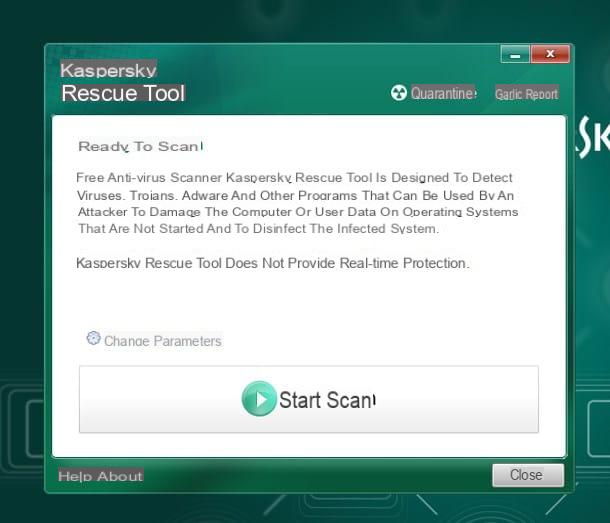
If, for some reason, you have not benefited from the previous solution, since the hidden virus prevents the correct installation of the antivirus program of your choice, you can try to bring everything back to normal via a rescue diskthe rescue disk.
This type of support allows the execution of a complete antivirus "outside" the operating system installed on the computer: in this way, it is possible to perform the analysis of files in complete tranquility, easily detecting viruses and malware hidden in all disks connected to the computer.
My choice, for this purpose, falls on Kaspersky Rescue Disk: this is a free version of the computer antivirus of the same name, which can be started from CD or from USB pendrive and offers a series of useful tools for analyzing and detecting malware present in files on disk (especially in system files), all with a very simple interface that can also be used by those who are new to computers.
How do you say? Do you really think you have found the right solution for you? Perfect, then let's get started! First, connect to the Kaspersk Rescue Disk website, close the initial window (relating to the request for feedback) and click on the button Download now to start the download of the image file (eg. kdr.iso).
Once this is done, burn the downloaded ISO onto a CD or create a bootable USB stick using one of the tools available on the network. If you have never done this before, I suggest you read my guides on how to burn ISO files (for creating a CD) or on how to create bootable USB stick, depending on the media you have chosen to boot the antivirus.
Once you have created the media that best suits your needs, insert it into your computer and reboot the system to enter setup BIOS / UEFI (if you don't know how to do this, follow the instructions I gave you in my guide on the topic) and set as the primary boot device the CD player or the USB port, always based on the support you have chosen to create previously. If you need help with that, you can refer to my tutorial on setting up the BIOS, which I wrote especially for you.

If everything went smoothly, you should see the writing appear on the screen Press ESC to load Kaspersky Rescue Disk: to immediately start the "live" support, press the button ESC keypad within 5 seconds from the appearance of the aforementioned message and, in the subsequent menus, first select the language English, presses the button Submit on the keyboard and repeat the operation selecting, this time, the voice Kaspersky Rescue Disk, Graphic mode.
Once the antivirus has been loaded into memory, you should see the complete interface of the same: what you have to do is affix the checkmark next to both boxes proposed in the initial window, press the button Accept to accept the license terms and to start a full system scan using the default settings, click the button Start Scan which should appear a few seconds later.
If, on the other hand, you need to find hidden malware only on a certain disk, or you want to add other external storage media to the analysis, click on the item Change Parameters and put the check mark next to the additional disks to be analyzed. To add new items, you need to click the button instead Add Object…. Once you have made the necessary settings, you can press the button Start Scan to start the system analysis.
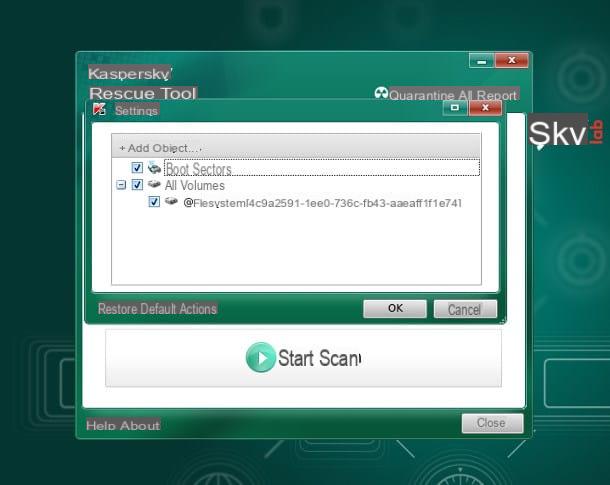
To view, even during the scan, the malicious files detected and / or moved to quarantine, you can press the buttons at any time Report e Q, located at the top right.
At the end of the analysis, which could also take a long time, Kaspersky will show a summary screen containing the actions taken automatically or any requests on what to do on the malicious files detected: usually, it is possible to move the files to quarantine (quarantine), diarrhea (chub) or delete them (delete).
Keep in mind that, in case of need, you can access the contents of the disks connected to your computer at any time by clicking on the icon Volumes, browse the Internet by clicking on the icon Firefox or take advantage of the tools offered by the rescue disk (terminal, screenshot, file manager, and so on) by calling them from the main menu of the system, accessible via the button in the shape of a K located at the bottom left. When you're done, you can restart your computer via the menu K > Leave > Restart.
How do you say? Would you need something that can make you act even more deeply, perhaps in a more "professional" way? Then I advise you to contact Comodo Rescue Disk, a rescue disk based on the antivirus of the same name and rich in features and tools for deep cleaning of files. I told you about it in detail in my guide on how to delete viruses from your PC without formatting.
Scan online
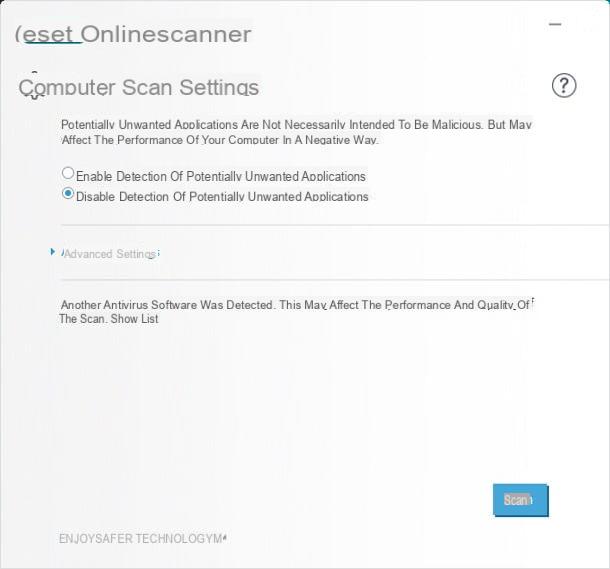
You have no way to install a different antivirus solution than the one you already use and you don't have the necessary tools to create a Rescue Disk? As a last resort, you can try to make one online virus scan using special software. For this guide, I have chosen to suggest you Eset Online Scanner, the free tool dedicated to online analysis promoted by the software house of the same name (the "mother" of antivirus solutions such as NOD32, so to speak).
To use it, connected to the main web page of the application, press the button Scan Now and wait for the supporting software (eg. esetsmartinstaller_enu.exe) is downloaded to your computer. At the end of the download, launch the downloaded file, press the button Accept, by pressing the button Yes and indicates whether to activate (enable) or less (disable) detection of potentially unwanted applications o potentially unwanted applications (i.e. of those programs often installed, for advertising purposes, together with other free software) and press the button Scan to enter the system analysis preparation phase.
Note: if necessary, you can use additional options (such as detecting potentially unsafe applications, automatic cleaning of threats or using a proxy to access the Internet) by clicking on the entry Show advanced settings.
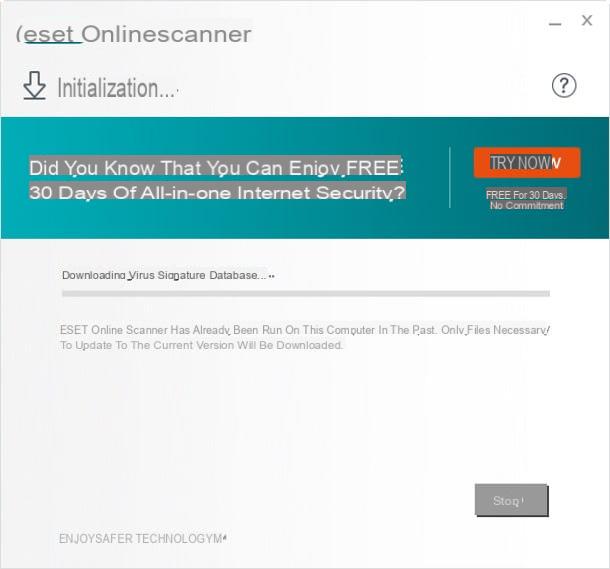
At this point, Eset Online Scanner should immediately start downloading the database containing the virus signatures and, after this procedure, start the analysis phase: you can follow the progress using the specific progress bar that is shown on the screen.
If this solution has not been able to fully convince you and you are afraid that it has not been able to find all the active threats on your computer, you can rely on other free software, designed for online file scanning: I told you about it in detail in my specific study. .
How to find hidden viruses on Mac
You did not find the information I provided in the previous lines useful, since you do not use Windows but have a Mac? Fortunately, macOS is not the target of viruses like Windows: in addition to being a less "coveted" system by cybercriminals, you should know that this operating system integrates predefined protections (eg GateKeeper) capable of preventing the execution of potentially harmful software.
However, if you experience some strange behavior on your computer, you can refer to my tutorial dedicated to the best Mac antivirus and perform a full system scan following the instructions in the guide. For your information, antivirus for Mac can also easily recognize viruses designed for Windows: in this way, it is possible to prevent the exchange of infected files (eg via USB stick) from other systems.
How to "stay away" from viruses

If you have come to read this far, it means that you have followed to the letter all the advice I have given you in the course of this guide and that, most likely, you have managed to find hidden viruses in your PC and to get rid of it permanently. Before concluding this discussion, however, let me give you some advice, so that you do not have to find yourself fighting again against strange behaviors and threats of various kinds that can endanger the integrity of your data and your computer.
- Keep system protections active - the most modern versions of Windows and macOS use built-in security tools, such as the filter SmartScreen and User Account Control on Windows and the tool GateKeeper on macOS, which can prevent potentially harmful or infected software from running. Although, in practice, they may cost you a few more clicks, I recommend that you always keep these tools active to prevent programs outside your control from starting.
- Keep your antivirus updated - technology is evolving rapidly and, unfortunately, this also brings with it the evolution of the techniques that cybercriminals use to create and spread malware. For this reason, it is essential that the antivirus installed on the computer is always updated to the latest version available.
- Run trusted software - download and install on your computer only programs from certified sources, such as the Microsoft Store, the Mac App Store and the official Internet sites of the most famous commonly used programs. Strictly avoid the installation of pirated software: the latter is an immense vector of viruses, spyware and all other types of threats.
- Beware of "bundled" programs - as you surely know, many free programs promote the installation of unwanted programs or spyware, purely for profit. Pay particular attention to the screens proposed during installation and the check marks set: where possible, avoid the installation of sponsored software, toolbars and other junk programs.
- Use common sense - even if the installation of infected software is the most common vector for the spread of malware, it is not the only means of transmission: just open a malicious email attachment, insert a storage medium (such as a USB or microSD key) or do other “risky” operations, to find oneself the victim of extremely unwelcome guests. Therefore, try to use the greatest degree of prudence possible and avoid opening attachments whose origin you do not know (or do not expect), connect to the computer devices of people you do not know or connect the PC to local networks (Ethernet or Wi -Fi) of strangers: you'll see, the computer will be able to thank you!
Article produced in collaboration with Avira.
How to find hidden viruses on your PC