Check installed apps
The first aspect you need to pay attention to don't get spied on WhatsApp concerns the apps installed on your terminal: some of them, in fact, could send data on the activity carried out through the smartphone (including accesses to WhatsApp, the amount of data exchanged and other information) without its legitimate owner being knowledge.
In principle, the apps that can be used for the collection of this type of information are mainly "legal" and designed for parental control, that is, to be used by parents as a control tool towards their children: this does not, however, mean that someone very curious could install something similar on the victim's device, perhaps in a moment of distraction, so that they can receive everything that interests them without any kind of effort.
Among the best known apps of this type are Qustodio, Cerberus Screen Time e Norton Family Parental Control, available for both Android and iOS: if you remember, I have already had the opportunity to tell you about some of them in my tutorial on how to spy on Android to control minors.
How do you know if someone has installed such an app on your device? First, you need to check if they exist elevated app (on Android) or custom configuration profiles (on iOS): for the parental control to work properly, the monitoring app must have been previously enabled to obtain advanced access permissions.
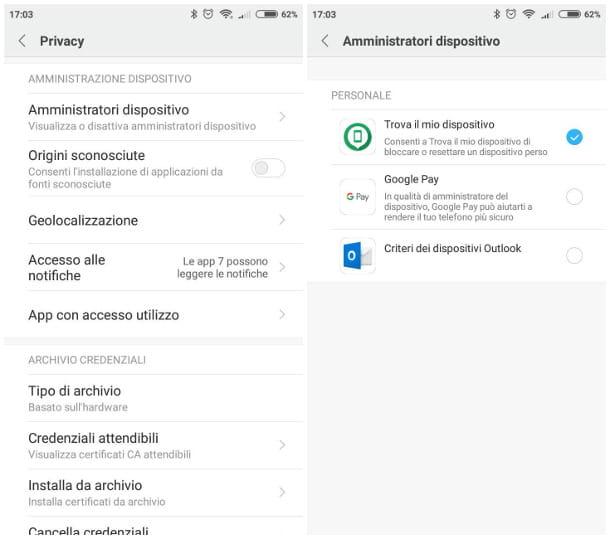
So, if you use a terminal Androidpigia sull'icona Settings placed in the drawer (i.e. the menu where all the installed apps reside) of your device, then go to the section Security> Administer Device (Or Other settings> Privacy> Device administration): look carefully at the proposed list, check for any "suspicious" apps and, if there are any, disable them by removing the check mark next to their names.
Once this is done, also uninstall it without hesitation with the procedure you would usually use: if you have never uninstalled an app from Android and do not know how to proceed, I urge you to consult my specific tutorial on the subject.
If you have a iPhone, what you need to do is check the custom profiles: first, tap on the icon Settings located on the home screen of the device, then select the items Generali e Management device and check for the presence of profiles associated with "suspicious" apps in the proposed list.
If these profiles actually exist, first uninstall the associated app, then reported in the aforementioned section and, after touching the item relating to the custom profile of the app just deleted, presses the button Eliminate profilo, type the security code you have set up on iOS and, finally, tap the button Delete.
If the Device Management item is not present among the options in General, then you can rest assured: your iPhone does not have apps installed that require "special" permissions.
Check for spy apps
Another category of apps that you need to be particularly careful of, if you want to protect yourself from the possibility that someone might spy on your WhatsApp, is that of spy-app. As the name itself implies, this type of software is designed with the specific intent of stealing information without having permission: in the vast majority of cases, such apps only work if the terminal in question has been subjected to the procedure of root (For Android) or that of jailbreak (For iPhone).
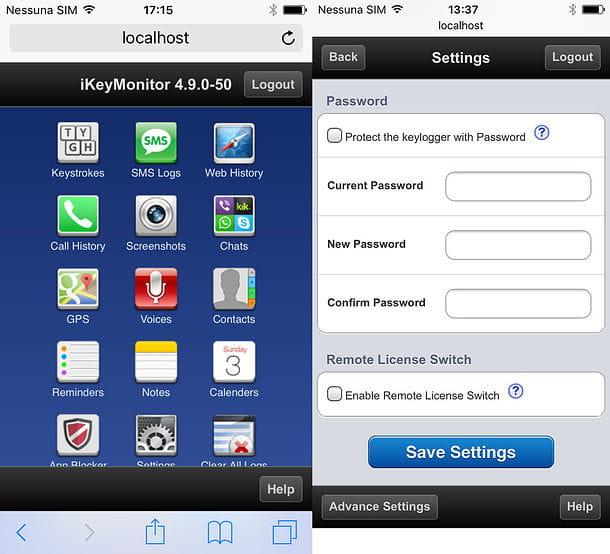
Among the best known exponents of this category, still able to obtain excellent results for any spy, I can quote you iKeyMonitor for Android and iOS: this is an app that can monitor the frequency with which you send messages, capture screenshots, record phrases and words typed on the keyboard and much more. I told you in depth about this software in my guide dedicated to apps to spy on WhatsApp.
As far as detection is concerned, spy apps can be decidedly subtle: many of them, in fact, have the particularity of not appearing (at least not with their own name) in the list of apps installed on the device, nor among those running, therefore they can escape the “classic” checks carried out by a not very expert eye. However, this does not mean that there are procedures that allow you to reveal their presence, to trace the name used and to deactivate them through a specific configuration panel: below I illustrate the most effective.
- Start the browser of your device and try to connect to the addresses localhost: 4444 or localhost: 8888: many spy apps use them to hide their configuration panel. This panel allows, among other things, to deactivate the spy app: once this is done, you just have to uninstall the “offending” software with the procedure that best suits your device.
- If the above procedure has not worked, try starting the dialer (i.e. the screen for manually dialing the phone number) and enter the code * 12345: this is another method to access the possible configuration panel of the spy app.
- In case you have a terminal Android on which the root procedure was carried out, I suggest you start SuperUser / SuperSU and to check for any spy apps among those that have obtained root permissions. If your search is successful, immediately revoke the aforementioned permissions to these apps and proceed with the uninstallation through the classic procedure provided by Android.
- If, on the other hand, you have a iPhone jailbroken (i.e. jailbroken beforehand), start Cydia and check if any suspicious apps are installed on the terminal: if so, delete them immediately.
Check your WhatsApp Web sessions
Web WhatsApp, if you had never heard of it, it is nothing more than the version of WhatsApp that can be used via the browser: just make a simple association between the smartphone and the PC to be able to chat quietly with your contacts, using the mouse and keyboard. If you need further details on this, I invite you to consult my specific tutorial on how to use WhatsApp Web.
Although WhatsApp Web is an official tool designed for legitimate purposes, it can turn into a method of being spied on, mainly due to the option Stay connected (which prevents the definitive disconnection of the account after closing the browser): in fact, a few seconds of distraction are enough to ensure that the meddler on duty takes possession of the victim's smartphone and makes the association between the WhatsApp app the latter and your computer, taking care to check the offending option.
Once this has been done, it is extremely easy for the spy to read conversations without permission, whenever he wants: he just needs to connect to the WhatsApp Web page, taking care to read the new messages after the legitimate recipient, to act undisturbed. and hide its presence.
Recently, the WhatsApp team wanted to partially remedy this eventuality: every time WhatsApp Web / WhatsApp for PC is associated, a warning notification is sent a few hours later on the device hosting the "original app" ". As I have already told you, however, this is only a partial remedy, as the notification may escape you or not appear at all.
In addition, another protection system introduced by WhatsApp is the confirmation of access to WhatsApp Web / Destkop through a biometric authentication method; the same, however, must have previously been set on your device as a system for unlocking the device. If not, you will not be prompted for confirmation to scan the QR code.
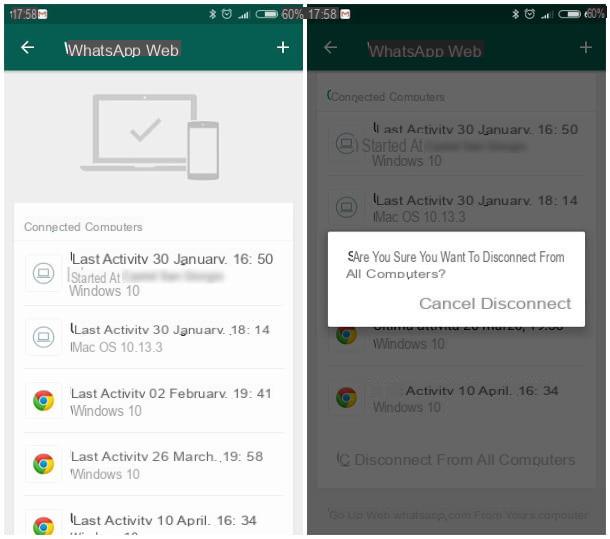
How, then, to check WhatsApp Web and understand if there are associations with PCs that should not be associated instead? Nothing could be simpler: first start WhatsApp, then access the chat list, press the button ⋮ su Android or button Settings on iOS and select the item Web WhatsApp from the menu proposed on Android or WhatsApp Web / Desktop from the panel iOS: in this way, the entire list of connected computers is displayed, complete with information about the browser, operating system and the location from which you accessed.
If you notice suspicious activity in this list, press on the item related to the computer that does not convince you and, subsequently, on the button Disconnect; if, as an additional security measure, you intend to disconnect from all the computers to which your WhatsApp is associated, tap the button Disconnect from all computers and presses the button again Disconnect.
Enable two-factor authentication on WhatsApp
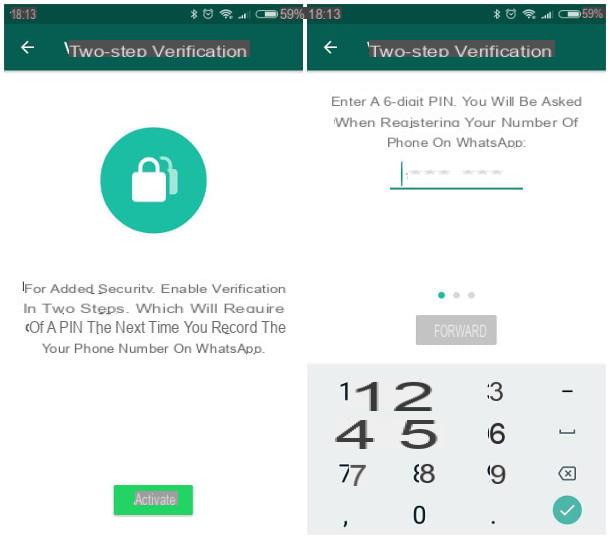
As you surely know, to log in on WhatsApp it is sufficient to have a phone number enabled to receive SMS: this means that, if someone comes into possession of your SIM without permission, they would potentially be able to make a new association. to WhatsApp and to spy on your conversations.
In order to avoid this, you can enable two-step verification: in this way, in addition to the telephone number, a personal PIN will be required to be entered when activating the account to finalize the authentication operation. Activating this feature is simple: start WhatsApp on your device, access the chat list, then tap the button ⋮ and select the item Settings from the proposed menu, if you are on Android, or press the button Settings, located in the lower right, on iPhone.
At this point, you simply have to tap on the item Two-step verification, by pressing the button Activate, and follow the on-screen instructions to set up a PIN to 6 figures to be used during registration; take care to remember the PIN set in this way or to keep it in a safe place (e.g. a password manager) since, without it, you will no longer be able to activate WhatsApp after uninstalling it or changing the device.
Disable the display of notifications on the lock screen
A method by which someone could spy on you without your permission, without even touching your smartphone but simply having it under an eye, is to "read" the messages received through the notifications that the app generates on the lock screen. Worse still, always using notifications, someone could associate your number with the WhatsApp app installed on their smartphone, thus having free access to all your conversations: the authentication procedure, in fact, requires the entry of a code received via SMS , which can be viewed without unlocking the phone if notifications are enabled on the lock screen.
Obtaining this inconvenience is very simple: just disable the display of SMS and WhatsApp notifications on the lock screen, following the instructions that I am going to specify below.
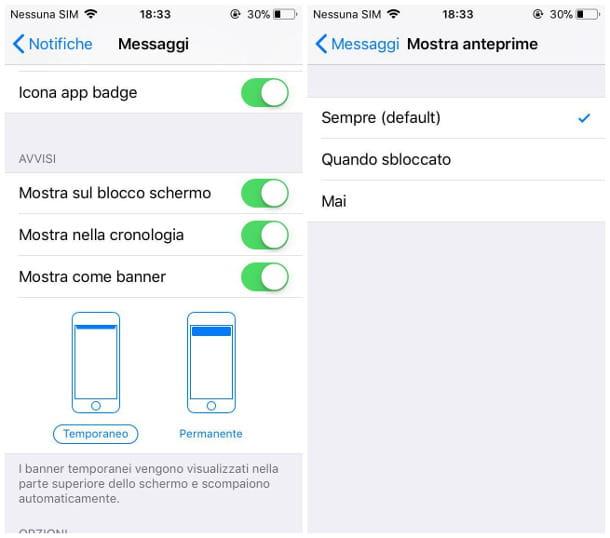
- Android - unfortunately, as far as Android is concerned, I cannot show you a general procedure that allows you to selectively inhibit notifications from the lock screen, since not all versions of the operating system support it. Alternatively, I can advise you to disable all notifications from the lock screen: don't worry, they will be there waiting for you as soon as you unlock your device. Proceeding is very simple: tap the button Settings, identify and select the item Audio and notifications and tap on the item With locked device placed in the box Notifications, then select the option Don't show notifications at all from the small menu proposed. In some operating systems, for example MIUI (the version of Android installed on Xiaomi devices), you can instead hide only the notifications relating to SMS and WhatsApp: press the icon Settings, select the items Notifications & Status Bar> Application Notifications, tap on the item Messages and move up Disabled l'interruttore accanto alla voce Lock screen notifications. Return to the previous screen and repeat the operation for the item WhatsApp.
- iPhone - to hide message previews, tap on the icon Settings, then select the item Notifications, then the voice Messages, and move up OFF the stalk at Show on lock screen. Finally, tap on the item Show previews on the same screen and select the option When unlocked. Once this is done, go back to the screen Notifications and repeat the same steps for the voice WhatsApp.
Use a secure unlocking method
Now that you have hidden notifications from the lock screen, you should set up an unlock method for your device that cannot be easily bypassed - in other words, you need to make sure that you and you alone can access your device after locking it. In this regard, I recommend that you first of all avoid the combination (the so-called "unlock pattern"), ie the operation of "drawing" on the screen in order to be able to use the device.
In reality, it is not very easy to unlock without knowing the aforementioned sequence (as the device is locked in time after a series of wrong attempts), however it can be relatively simple to trace the sequence itself, thanks to the track left by the fingers on the screen of the device: in particular, this is particularly evident in the case in which, for example, the unlocking is carried out with fingers that are not perfectly clean or immediately after holding the smartphone close to the ear for a long time.
The same goes for the Unlock PIN / password: also in this case, the device is blocked after a series of incorrect attempts, however I advise you to set a code that is not easily understood by those who know you. Therefore, you should avoid your date of birth, the date on which you began the relationship with your partner, the name of the latter and, in general, the information that those who know you at least a little may be aware. .
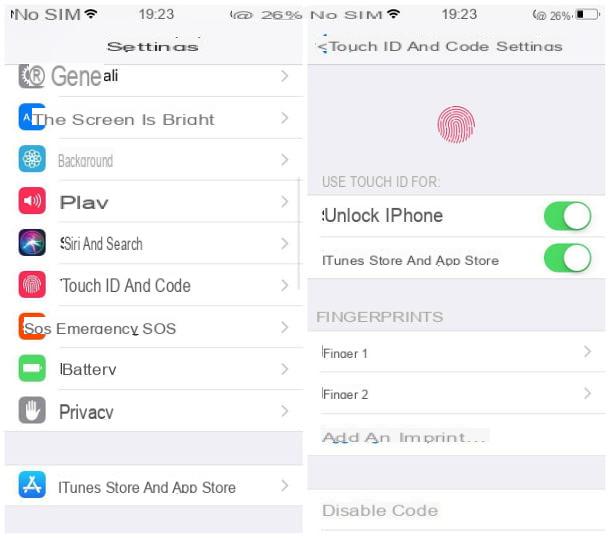
If the possibility of using a medium-complex PIN / password is not to your liking, I recommend that you contact an unlocking system biometric, using one of the sensors / chips definitely on board your device. Yes, therefore, when unlocking via Fingerprint (on Apple devices it is known by the name touch ID), iris scanning o face recognition (for Apple Face ID): the possibilities of overcoming similar mechanisms without being the owners of the device in question are practically very close to zero!
To set or change an unlock method, if you use Android, you simply have to go to the Settings and select items Security> Screen lock, choose the desired unlocking method from the list and proceed with the configuration following the instructions on the screen. Regarding iOSinstead, the right sequence to follow is Settings> Touch ID / Face ID and passcode: enter the unlock code when requested, then move to ON the stalk at Unlock iPhone in the box Use Touch ID / Face ID for: I gave you more information about this procedure in my guide on how to unlock iPhone without a passcode.
Clearly, the same goes for all computer on which you configured Web WhatsApp: you prefer biometric recognition by scanning your fingerprint or facial recognition and, if this possibility is not foreseen by your computer, be sure to set a password that is difficult to "guess" to access the operating system, so as to keep it away from prying eyes and avoid getting yourself spy on WhatsApp Web without realizing it.
Here on my blog you can find interesting insights on this topic: first of all, I recommend that you choose a secure password by following all the advice I have given you in my dedicated in-depth study, and then physically protect your computer with the chosen password using my tutorials specific about how to put password on PC and how to set password on Mac.
Run a malware scan
Have you read with commitment and dedication everything I have advised you so far, but are you still afraid that someone may be able to keep an eye on you, without you realizing it? Don't worry, I have some other valuable tips in store for you that can help you sleep more peacefully.
To start with, especially if you use Android and / or the PC to access WhatsApp, it is good practice to do one antimalware scan at regular intervals, so as to keep you safe from other insidious threats: unfortunately, today there are numerous software and applications useful to cause large data leaks from the devices on which they are installed, and which unfortunately do not exclude the most used messaging app at world.
Therefore, in order to don't get spied on WhatsApp completely unconsciously, I advise you to install an efficient antivirus on your Android terminal or on your PC, to always keep it updated and to carry out (or schedule) scans at regular intervals: if you do not know what to choose, I refer you to the advice that you I have provided in my guides to the best antivirus for Windows, and the best antimalware solutions for Android.
Use secure passwords for the cloud

Choosing a secure password to protect your device is always a practice to pay attention to but, speaking of WhatsApp, this also extends to cloud spaces: Google Drive, Google Photos e iCloud, just to give you a few examples, they can become a source of information and news for those who want to snoop into your private life.
To be more precise, both Google Drive and iCloud, depending on the device in your possession, store backups of WhatsApp conversations by default, as well as Google Photos and iCloud itself could automatically save the photos on your device, including those received. via WhatsApp. Consequently, be sure to use one strong password and secure enough to protect the aforementioned cloud spaces, and all other similar services that you use on your devices: you can find specific instructions on this in my tutorials on how to change Google password and how to change iCloud password.
Avoid root and jailbreak
Android smartphones, as well as iPhones, can be customized in a very relative way: although both operating systems can be subject to more "profound" changes than those visible to the user, also thanks to apps that can make them in a few seconds, such potentialities are somehow “blocked” by the factory and made invisible, so as to protect the safety of the device, the user and the stored data.
For a long time, however, these limitations have been overcome thanks to two precise mechanisms of action, respectively Android e iOS: root and jailbreak. Although in a distinctly different way, both of these systems allow the user to obtain special permissions, accessing blocked parts of the operating system, with the possibility of installing apps that modify them without too many complications.
In principle, getting root permissions on Android means installing apps SuperSU / SuperUser, able to access files and parts of memory protected by the system (and allow other apps to change them as well), while jailbreaking iOS consists in installing the alternative market Cydia, unlocking "forbidden" parts of the operating system and allowing apps from the aforementioned store to access it.

Bypassing the limitations imposed by manufacturers in this way may seem like a good thing, and in some cases it may even be, however it represents a not insignificant security problem, especially for data integrity.
Leaving aside for a moment the possibility of destroying the smartphone and voiding the warranty, keep in mind that the root and jailbreak expose very delicate data and information to apps that could have purposes other than those for which they seem to be designed. As I explained to you a little while ago, for example, the spy apps dedicated to the theft of information from WhatsApp require root permissions or jailbreak.
So, as an additional measure to avoid being spied on WhatsApp, don't root or jailbreak on your smartphone and, if you have already done so, cancel the change as soon as possible: as regards the root, you can proceed to uninstall SuperSU / SuperUser simply by starting the app and selecting the specific option, while as regards the jailbreak you have to follow a slightly more complex procedure, which I have explained to you in detail in my guide on how to remove the jailbreak.
Other useful tips

Before concluding our speech, I would like to give you what seems to be obvious advice but which, all too often, we end up ignoring: the first of these is do not lend smartphones and PCs to strangers!
If you have read all my guide carefully, you are surely aware of the fact that spying on WhatsApp can be difficult in theory, but that everything changes when the attacker finds himself in the hands of the unfortunate victim's device: it really takes a few minutes to install and configure an anti-theft app, a spy app, to associate with WhatsApp Web or, if we are talking about computers, to install a remote control program and make it invisible to both the user and the antivirus (this type of application, in most cases, it is considered safe).
Always keep in mind that lending your phone or computer to someone you don't know, or to people who don't have your full trust, potentially exposes you to the risk of being spied on, and not just through one of the methods I explained to you in the course. of this long but interesting study: thinking about it better, if you are the one who puts the device in the hands of those who shouldn't have it, why should the latter hesitate to open your WhatsApp and read the conversations? As they say ... opportunity makes the thief!
Other measures, if we want trivial, that can increase your privacy level on WhatsApp are the deactivation of online status (to prevent other users from knowing when you are connected to the service) and the deactivation of read receipts (the infamous blue ticks): you will find explained how to proceed for both operations in my tutorials on how to remove online on WhatsApp and how to disable blue ticks on WhatsApp.